One thing that I have learned is that no security measure is solid other than a computer without any ports, no screen and no NIC. If you want to have a connection to the internet you will be exposed to a massive amount of attacks. Therefore it is more important to detect attacks other then desperately trying to avoid vulnerability. You should be well protected but noticing that you have been hacked is just as important.
Plesk 12 has a nice addition as it comes to security. I’ve talked about security in this and this post. Now I will continue with some nice features of Plesk 12.
Modsecurity
If you upgraded your version of Plesk from 11.5, Mod Security will probably be optional. Mod Security is an application firewall that detects malicious code and prevent it from being ran. If you want this protection enable and install Mod Security. You’ll have three options: Disabled, Detect and Prevent.
Disabled needs no explanation
Detect Only will log any detected incident.
Prevent will actively try to prevent code from being run. It has impact on performance so be sure that you’ll enable it only if you server can handle it. You can tweak the settings so that there is a fast check if you have a lot of visitors. If you however want a thorough scan you can select that also.
Mod security works with a set of rules. This ruleset is updated regularly. By default the set of rules present in Plesk is a simple. This makes the effectiveness a little less but performance is maintained and security is improved over having no mod security. If want a very secure environment you can select to OWASP core set. This is a more thorough set but none the less a very good protection. You can optionally pay for a subscription for a professional service. Use this only if the basic ruleset is not good enough for you.
It is wise to update the ruleset once a day. I often see new updates and 0-day vulnerabilities will be patched quicker. The impact of the update process is small and the gain in security is high.
Fail2Ban
When you have a small server like me, with only a few site and look at the logs, you see a lot malicious traffic. All sorts of port scanning, robots, crawlers and hackers. This traffic only increases on server with a high user load. There are lists of username, password combination that bots are trying at any site. If you have an account on a hacked site and your username and password combination is exposed you do not want this to actually be exploited. Let alone your users. Not all companies disclose security incidents which makes it hard to know if your credentials are on some list. If you don’t have a unique set of username/password combination for every site that risk is real.
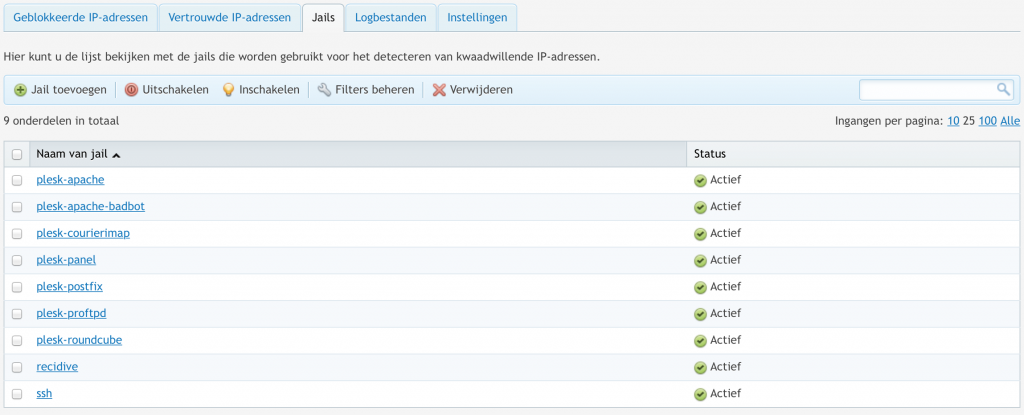
Plesk 12 has this incredible feature call Fail2Ban. This extension automatically bans these threats by IP-address. The default settings are very loose but this can be improved. Fail2Ban can built jails to detect login attempts and so forth. First install this feature and see my config below.
First you’ll have to enable jails. Jails are no more than automatically looking at logs. The logs are scanned and if an IP-address attempts multiple malicious actions in a certain period, that IP gets blocked. I would recommend to enable jails on all available services:
Apache jails will check of failed authentication or time traveling. Badbot detects fraudulent bots. You can check what a jail does by looking at the Filters tab.
By default Fail2Ban will detect 7 attempts within 10 minutes and then bans that ip for a period of 15 minutes. I personally think that a 15 minute break is way to weak. Also the 10 minute range is to short. Will users will keep on trying to logon after 7 attempts? They will contact you anyway to reset their passwords. So releasing their IP is then just part of the deal. As I basically work alone on this server I lowered the number of failures. Next I have expanded the time frame in which to look for a attempt to 900 seconds. The ban time should be at least a year. Imagine that those bots are built to try every 10 minutes with 7 login attempts. That will be 144 times 7 login attempts a day. That will be a 367.920 attempts a year when with my settings you’ll only have a small number of no more than 5. Imagine that such a organization has 10 ip-addresses. That is a massive number of attempts without you probably ever noticing one of them if you do not look at the logs. That’s why I configured a ban period of 31536000 seconds. That is precisely one year. Even for a server that has only been up for one week there are already 10 ip-addresses banned. That is a quite large attack surface been taken care of. You can configure a ban period that is there forever to make it negative. So if you configure a ban period of -1 seconds the IP address will not be released.
Of course this impacts performance. You’ll have to decide for yourself if this is worth it for you. In my case it is. But I do not host any high profile sites.
There is another downside for the implementation of Fail2Ban in Plesk. If you whitelist an IP-Address that has been blocked all blocked IP-Addresses will be released. Furthermore if you restart your server the blacklist will be release also.
WordPress toolkit
You may have noticed the new WordPress toolkit icon in the Plesk Admin panel:
This is a vital new function of Plesk 12. Security flaws in common web application can be exploited because they are not patched. With WordPress Toolkit you can update version of WordPress. You can also update plugins and themes. But it doesn’t stop there. You can also enhance security by removing the built numbers from all relevant files. You can tighten security on the wp-include and wp-content directories. The attack surface will be tremendously reduced. And the best thing is that you can see all installations even though you did not install them using Plesk. Having said that you can thus manage all your WordPress installation in one console. It is an incredible powerful addition and I wouldn’t want to miss it again.