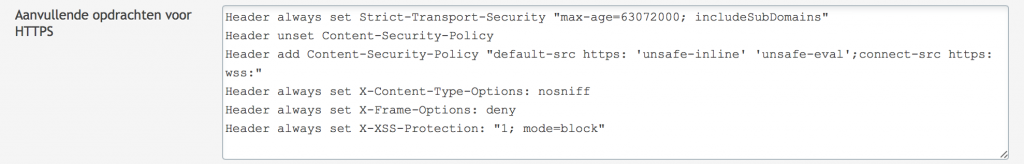
Plesk 12 comes with support voor Dovecot Secure IMAP server. This is a great improvement on the Courier IMAP server. I personally prefer Postfix for SMTP. You can configure Postfix in a very secure manner. In this post I will discuss how to configure Dovecot and Postfix and to configure Roundcube webmail for additional support.
Dovecot
Dovecot supports IMAP4 and POP3. I decided to disable POP3 as it is inferior to IMAP4. If you do want POP3 enabled you should alter the configuration. I disallowed a number of insecure ciphers. I disabled plaintext authentication as it is highly insecure. Note that even though you client is using SSL you can still be vulnerable to attack if Plain text authentication is enabled. Next I changed to directory for the certificate.
First install Dovecot if you haven’t done so. Establish a SSH connection to the server en vi the file:
/etc/dovecot/conf.d/01-servername.conf
01 makes it the last applied file. Adjust the content to your liking:
protocols = imap ssl_cipher_list = EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS:!RC4 ssl_prefer_server_ciphers = yes disable_plaintext_auth = yes ssl_cert = </etc/dovecot/private/certificate.pem ssl_key = </etc/dovecot/private/key.pem
This configuration encrypts IMAP4 traffic, disabled plain text authentication and enables a verifiable certificate. It diables a number of insecure ciphers and prefers better ciphers.
Postfix
Postfix is used by a massive amount of mail servers. Postfix by default is not configured in a safe manner. To enable Postfix to contact the rest of the world in a safe way you should enable certain ciphers. Furthermore you shouldn’t configure your Postfix server with EDH Ephemeral Diffie–Hellman. Most servers don’t support it yet which would lead to undeliverable mails. Instead use the Diffie-Hellman key exchange. You first need to create a 512 bit key exchange parameter file and a 1024 bit key exchange parameter file. Please note that a larger key length will result in a serious CPU penalty. To generate the files enter the commands below.
openssl gendh -out /etc/postfix/dh_512.pem -2 512 openssl gendh -out /etc/postfix/dh_1024.pem -2 1024
Next configure Postfix’s main.cf file:
vi /etc/postfix/main.cf
Remove the conflicting lines and add the lines below:
# TLS parameters smtpd_tls_cert_file = /etc/postfix/certificate_2014.pem smtpd_tls_key_file = $smtpd_tls_cert_file smtpd_tls_dh1024_param_file = /etc/postfix/dh_1024.pem smtpd_tls_dh512_param_file = /etc/postfix/dh_512.pem smtpd_tls_eecdh_grade = strong smtpd_tls_protocols= !SSLv2, !SSLv3 smtpd_tls_mandatory_protocols= !SSLv2, !SSLv3 smtpd_tls_security_level=encrypt smtpd_tls_mandatory_ciphers = high tls_preempt_cipherlist = yes smtpd_tls_mandatory_exclude_ciphers = aNULL, MD5 , DES, ADH, RC4, PSD, SRP, 3DES, eNULL smtp_tls_security_level = may
This will not be the most secure configuration. But please keep in mind that enforcing very high security standards will come at a high price.
Roundcube
When you altered the configuration above you need to restart the service of Postfix and Dovecot:
/etc/init.d/postfix restart /etc/init.d/dovecot restart
When that is done your default Roundcube won’t work no more. This can be fixed by doing the following:
vi /usr/share/psa-roundcube/config/defaults.inc.php
Change the following values:
// IMAP // ---------------------------------- // The mail host chosen to perform the log-in. // Leave blank to show a textbox at login, give a list of hosts // to display a pulldown menu or set one host as string. // To use SSL/TLS connection, enter hostname with prefix ssl:// or tls:// // Supported replacement variables: // %n - hostname ($_SERVER['SERVER_NAME']) // %t - hostname without the first part // %d - domain (http hostname $_SERVER['HTTP_HOST'] without the first part) // %s - domain name after the '@' from e-mail address provided at login screen // For example %n = mail.domain.tld, %t = domain.tld // WARNING: After hostname change update of mail_host column in users table is // required to match old user data records with the new host. $config['default_host'] = 'ssl://hostname.TLD'; @include "/etc/psa-webmail/roundcube/mailhosts.php"; // TCP port used for IMAP connections $config['default_port'] = 993; // IMAP AUTH type (DIGEST-MD5, CRAM-MD5, LOGIN, PLAIN or null to use // best server supported one) $config['imap_auth_type'] = DIGEST-MD5; // ---------------------------------- // SMTP // ---------------------------------- // SMTP server host (for sending mails). // To use SSL/TLS connection, enter hostname with prefix ssl:// or tls:// // If left blank, the PHP mail() function is used // Supported replacement variables: // %h - user's IMAP hostname // %n - hostname ($_SERVER['SERVER_NAME']) // %t - hostname without the first part // %d - domain (http hostname $_SERVER['HTTP_HOST'] without the first part) // %z - IMAP domain (IMAP hostname without the first part) // For example %n = mail.domain.tld, %t = domain.tld $config['smtp_server'] = 'tls://hostname.tld'; // SMTP port (default is 25; use 587 for STARTTLS or 465 for the // deprecated SSL over SMTP (aka SMTPS)) $config['smtp_port'] = 587;
This will restore the Roundcube functionality.