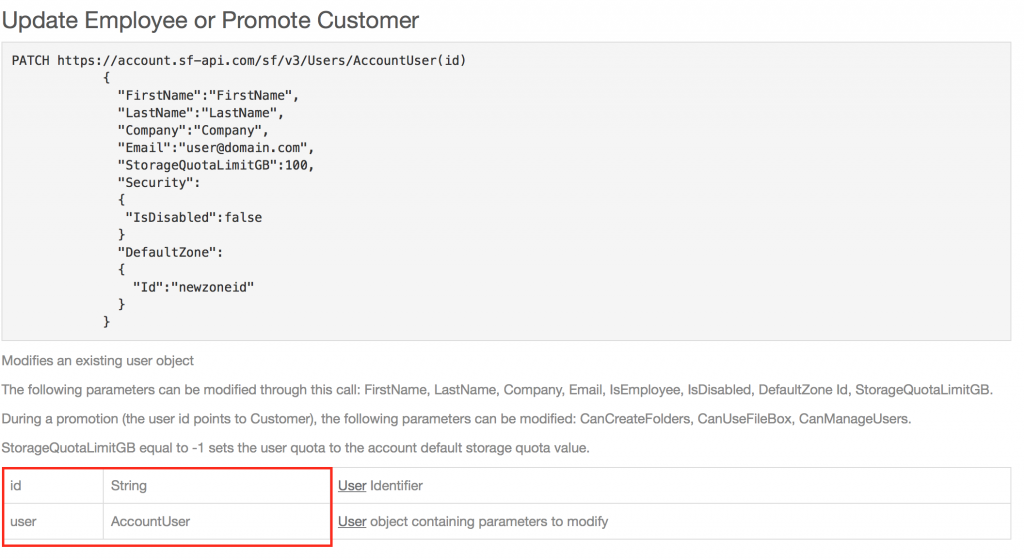
I just wrote an opinion about the Powershell module of Citrix ShareFile. Now let’s get to it. This is the fun part. You’ll have to take a close look at how Citrix describes things. So if you want to manage the StorageQuotaLimitGB field using Powershell, you can use the script below. I’ll get in detail about it.
Add-PSSnapin ShareFile
$SFClient = Get-SfClient -Name File.sfps
$User = Send-SfRequest $SFClient -Method GET -Entity "Accounts\Employees" | ?{$_.Email -match "EmailAddress@Domain.TLD"}
$Property = new-object ShareFile.Api.Models.AccountUser
$NewQuota = ([int]$Quota = (Send-SfRequest $SFClient -Method GET -Entity "users" -Id $User.id).StorageQuotaLimitGB) + "5"
$Property.StorageQuotaLimitGB = $NewQuota
$Uri = $user.url.OriginalString.replace("Contacts","Users/AccountUser")
$Result = Send-SfRequest -Client $SFClient -Method Patch -Uri $Uri -Body $property
If ($Result.StorageQuotaLimitGB -notmatch $NewQuota){Write-Error "Value is niet aangepast"}
This script will export all users and then select the user with the e-mailaddress specified. You can of course enter a string there with a specific value. Then it creates a new property with the value AccountUser. See it like this you want to edit this value but it is not in the Entity Users but one endpoint lower. It is in the entity AccountUser. AccountUser is below the entity User. If you for example would enter -Entity “Users”, the script will fail because the value StorageQuotaLimitGB is simply not present at that level. At first I got this wrong. So that’s why you set this value lower. It is described on the site of Citrix but just a bit cryptic. Look for this part of the text:
So then the script get the current limit and adds an additional 5 GB to that limit. This is caught in a integer. Than I get the URL. Please not that here in the EU we have a different link. This script is not impacted by that but this explanation is. ShareFile uses this link:
https://ShareFileDomainName.sf-api.eu/sf/v3/Users(ID)
Well if you use the Entity Users the link above will be used. As said above you’ll want to point to the endpoint AccountUser. So the script changes the current uri from contacts to this:
https://ShareFileDomainName.sf-api.eu/sf/v3/Users/AccountUser(ID)
That is the magic. Next the script sends a request to the REST API of ShareFile to apply the new StorageQuotaLimitGB. At last it checks if the change is actually applied. If it isn’t a error is written.