In an addition to my previous post I would like to add a few updates and improvements.
HSTS
While it is possible to add a line in the conf file. You can also use a nifty function in Plesk. Since Plesk 11.5 configuring the web server per site is possible. But before I take you to heaven I would like to add a few side notes. Be sure that if you use the includesubdomains flag, that all your subdomains support HTTPS. You can of course configure this per site, but if a browser connects to the parent site and receives the HSTS header, it will automatically connect for a long time to all subdomain using HTTPS. If one of your subdomain doesn’t support HTTPS and the user visited the parent site you’ll have a problem. You can of course exclude the IncludeSubDomains flag.
When logging in the Plesk Panel site you can configure the webserver. Go to Websites and Domains en click on Expand. Next click on configure webserver.
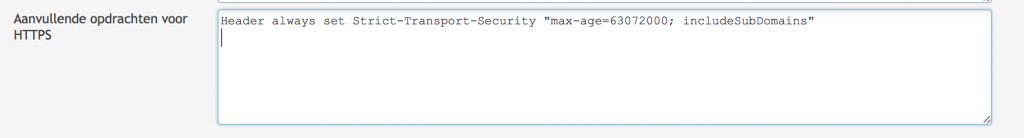
Scroll down to the end of the page and add the following line in the HTTPS settings:
Please mind the includeSubDomains switch
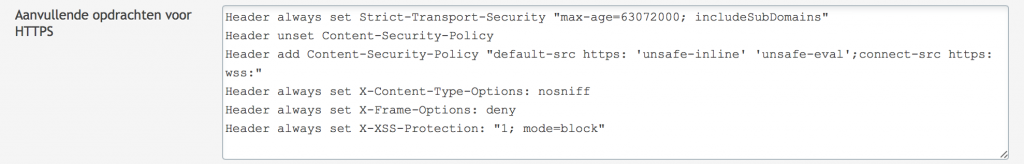
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains"
CSP
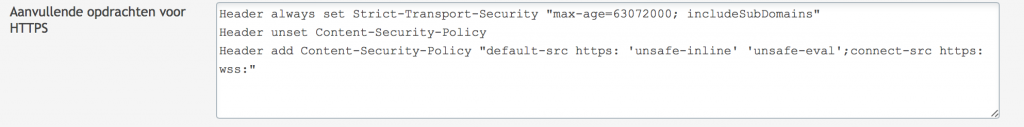
I recently learned about CSP. This make it impossible to have malicious XSS or other code being run from your site. For example if you have a script that is being referred to in the index of you site, it is harder to exploit the trust that you browser has in your site. You can very basically configure this using the same steps as above by adding another line in you HTTPS config
Header unset Content-Security-Policy Header add Content-Security-Policy "default-src https: 'unsafe-inline' 'unsafe-eval';connect-src https: wss:"
Please note that this is a very basic way to configure CSP. To further tighten CSP you can read this site. To enable full CSP you can replace about code with:
Header unset Content-Security-Policy Header add Content-Security-Policy "default-src 'self'"
Additional headers
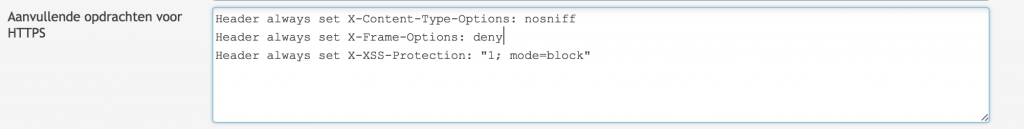
Other headers that can strengthen the security are:
Header always set X-Content-Type-Options: nosniff Header always set X-Frame-Options: deny Header always set X-XSS-Protection: "1; mode=block"
Please note that these headers may alter you website functionality. For example X-Frame-Options: limits frame redering. So if you have code that runs in a frame, there will be no output. My advise is to play around with these headers in your test environment. Above headers may be also used in HTTP. So you can add them to the HTTP headers. This is unlike HTST which of course has something to do with secure transfer.
You configure them in the same way as the headers above:
In my next post I will get into HTTP Public Key Pinning. This I still have to figure out myself so if I have some spare time I will test around a little bit. The support for this feature isn’t very broad. Only predefined list are currently supported. As always IE doesn’t support it yet. Firefox supports it since version 32. Chrome supports it since 2011. However there is no mainstream support for it as of now. HPKP will however be supported in the future so I want to be sure that by the time it is supported, I already comply 🙂
The complete header looks like this: